Issue with Get-NetFirewallProfile PowerShell cmdlet and netsh advfirewall command incorrectly displays Windows Defender Firewall state when configured with Group Policy
When running either the Get-NetFirewallProfile PowerShell cmdlet or netsh advfirewall command you may find they incorrectly display thee Windows Defender Firewall enabled state when the firewall is configured with Group Policy.
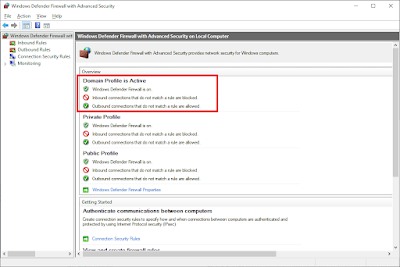
By default the Windows Defender Firewall is on
Disabling the firewall in the MMC displays as expected in the summary pane
Both netsh and PowerShell's Get-NetFirewallProfile correctly show the state as disabled.
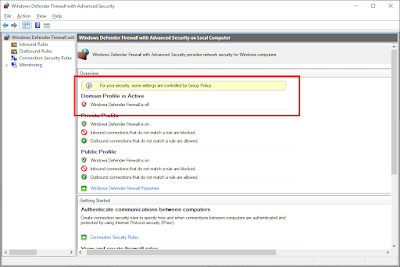
However when the firewall's Domain profile is disabled using Group Policy
You see that the user interface again updates correctly, and a message stating that Group Policy is in force
However, BOTH PowerShell and netsh incorrectly report the Firewall as being enabled.
The registry key backing this configuration is
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\WindowsFirewall\DomainProfile
DWORD
Enabled
Running Process Monitor from sysinternals it doesn't appear that either PowerShell or Netsh are looking at the group policy setting.
The solution to this is to run the Get-NetFirewallProfile cmdlet with the "PolicyStore" parameter set to "ActiveStore".
Get-NetFirewallProfile -Name "Domain" -PolicyStore "ActiveStore"







Comments
Post a Comment