Error message "Get-DfsnAccess : The requested operation is not supported" when using Active Directory DFS PowerShell module

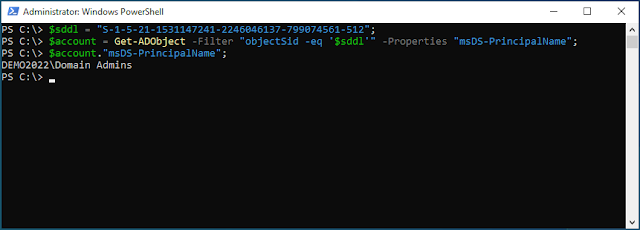
When using the Active Directory DFS PowerShell module's cmdlet Get-DfsnAccess you may see the error Get-DfsnAccess : The requested operation is not supported This can occur if you run the command with a path that points to a namespace or a version 1 folder. To clarify this cmdlet gets the view permissions on a DFS folder seen on the advanced tab. You'll notice that on a domain version 1 - shown as "Domain (Windows 2000 Server mode)" in the DFS user interface does not have an Advanced tab on its folders. If you're looking for the permissions assigned to the namespace seen on the "delegation" tab here. These permissions can be obtained by reading the "GrantAdminAccess" property of the Get-DfsnRoot cmdlet. Get-DfsnRoot -Path "\\demo2022.int\Domain2008"|SELECT -ExpandProperty GrantAdminAccess While you're here - Why not check out our Active Directory Documentation Tool ?